News Archive
 Harm Reduction
Harm Reduction
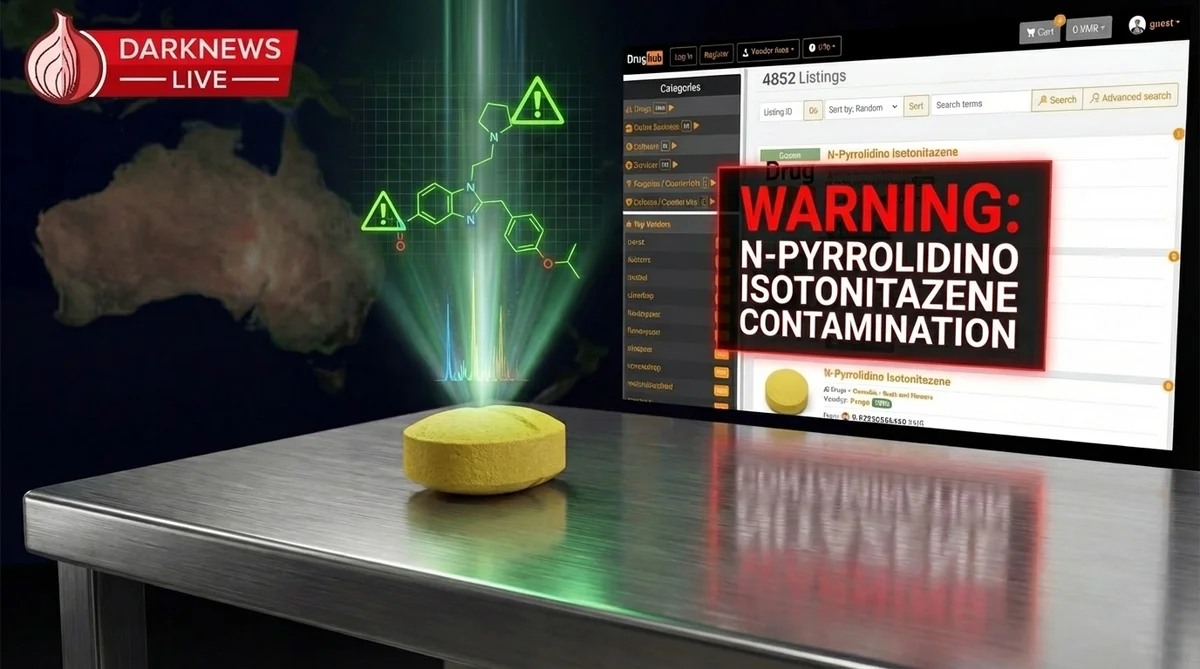
The Nitazene Threat: Canberra Detects Darknet Opioid 100x Stronger than Fentanyl
The 'Safe Supply' myth is dead. CanTEST analysis in Australia has confirmed the presence of N-Pyrrolidino Isotonitazene—a synthetic horror 1,000 times stronger than morphine—hidden in pills sold as Oxycodone. We analyze the supply chain and the fatal negligence of market admins who allow these listings to persist.
Read Report → State-Sponsored Threats
State-Sponsored Threats
The $10 Million Dox: U.S. Puts a Price on GRU Unit 29155 ('Cadet Blizzard')
The U.S. State Department has escalated the cyber war, offering a massive reward for the identification of the 'Cadet Blizzard' operatives. We analyze the attribution of this group to the GRU's 161st Specialist Training Center, their deployment of the WhisperGate wiper, and the massive OpSec failure that led to their indictment.
Read Report → State-Sponsored Threats
State-Sponsored Threats
Kinetic Killers go Digital: GRU Unit 29155 and the WhisperGate Wipers
They were known for poisonings and coup attempts. Now, Russia's most notorious wetwork unit has pivoted to cyber warfare. We analyze the DOJ indictment of five GRU officers, the deployment of WhisperGate, and the irony of Russian military hackers utilizing US-Navy technology to mask their tracks.
Read Report →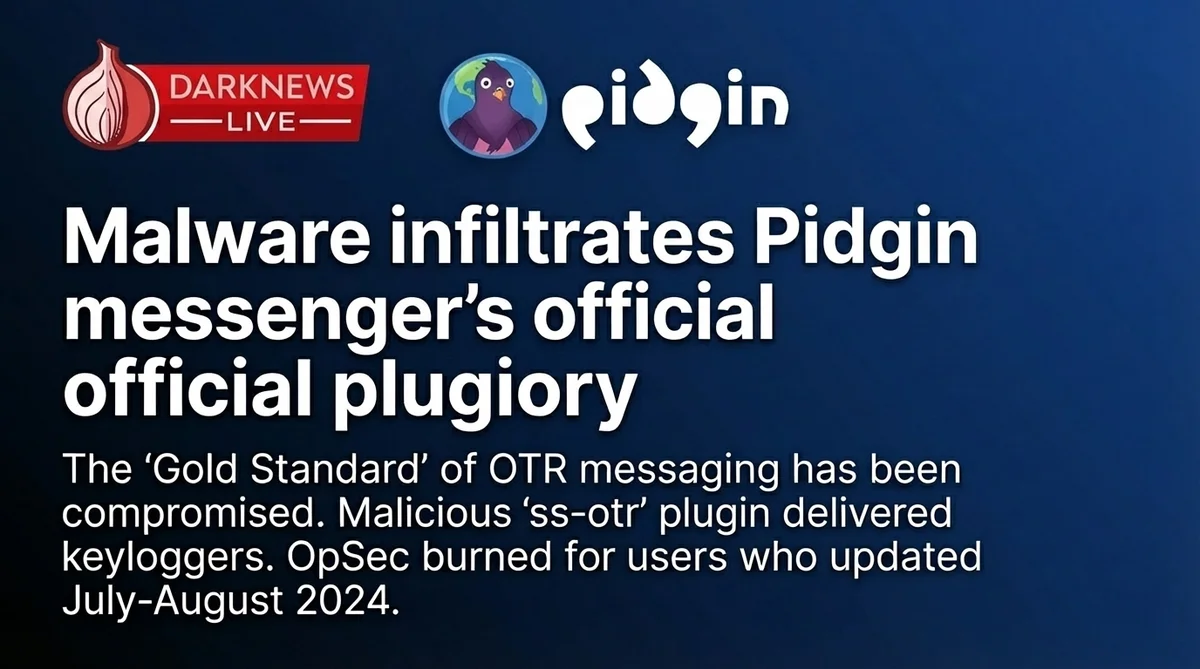 OpSec Alerts
OpSec Alerts
Supply Chain Poison: Malware Infiltrates Pidgin’s Official Plugin Repository
The 'Gold Standard' of OTR messaging has been compromised. For over a month, a malicious plugin named 'ss-otr' sat in the official Pidgin repository, delivering keyloggers and infostealers to privacy-seeking users. If you updated your plugins in July or August 2024, your OpSec is likely burned.
Read Report → Cybercrime Prosecution
Cybercrime Prosecution
The Physical Layer Breached: Latvian Karakurt Operative Extradited to U.S.
The FBI's dismantling of the Conti syndicate continues. Deniss Zolotarjovs, a 33-year-old Latvian national and alleged key figure in the Karakurt extortion group, has been extradited from Georgia to Ohio. We analyze the money laundering pipelines—specifically the use of high-volume illicit exchangers—that fueled this cybercrime engine.
Read Report →